When a website can be accessed via a clearnet and a .onion url, is there a benefit to making use of the .onion url?
Context:
I am considering pointing a “.onion” url to my instance (mander.xyz).
I did some tests with and it seems like mlmym works well with JavaScript disabled. Since JavaScript is often disabled in the tor browser, I could make the .onion url point at that front-end instead.
This would be fun to do, but I wonder if there is a practical benefit to the “.onion” url as opposed to simply accessing the clearnet url via the tor browser.
EDIT: I went ahead and created an onion URL to try out, but I would still like to know if there is an actual advantage to .onion urls:
http://mandermybrewn3sll4kptj2ubeyuiujz6felbaanzj3ympcrlykfs2id.onion/
One advantage I can think of right off hand would be domain blocks can be bypassed with an onion URL.
In the context of tor, a domain block would apply - for example - if the exit node’s ISP blocks the domain. But if the local network implements domain blocks, this would not affect the tor browser - is this correct? Or is it also possible to block domains locally even for tor browser users?
An onion domain does not use the clear net whatsoever. So the tor client machine contacts your machine directly (with 6 hops) from within the network and never exits out to the open internet.
I think staying inside the tor network helps reduce the load on exit nodes, which helps all tor users who need to access the clearnet. I think there is even a HTTP header that can be put on the clearnet site that will put a button on the tor browser that tells users that there is a onion available.
Ah - does the exit node participate at all when accessing a .onion? Or is it skipped altogether?
And the HTTP header thing is very cool, I did not know about that!
I have added the header to the site and it works!
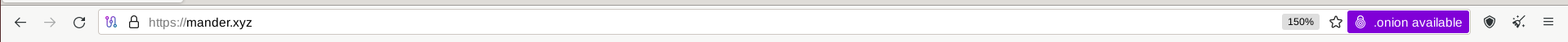
I just added the following line to the location / {} block in the https server section:
add_header Onion-Location http://mandermybrewn3sll4kptj2ubeyuiujz6felbaanzj3ympcrlykfs2id.onion/$request_uri;I think its just the non-exit nodes that are needed as long as the traffic stays inside the tor network, I dont think an exit node gets involved at all, but I’m not 100% sure
Yes this has several benefits:
- some users prefer not to reveal their IP to your server
- some users prefer not to be tracked by their internet provider (or by Google via DNS on Android, or by local wifi users or by who knows who)
- your onion site is censorship resistant (some users in Russia or else might need it)
- your onion can be ddos-resistent (if you enable POW)
- your clearnet site might be unavailable for other reasons (unrenewed DNS entry or expired certificate)


