TL;DW
LINDDUN card deck PDF for reference: https://downloads.linddun.org/linddun-go/default/v240118/go.pdf
I actually don’t agree with this video; and firmly believe it is more than a little biased.
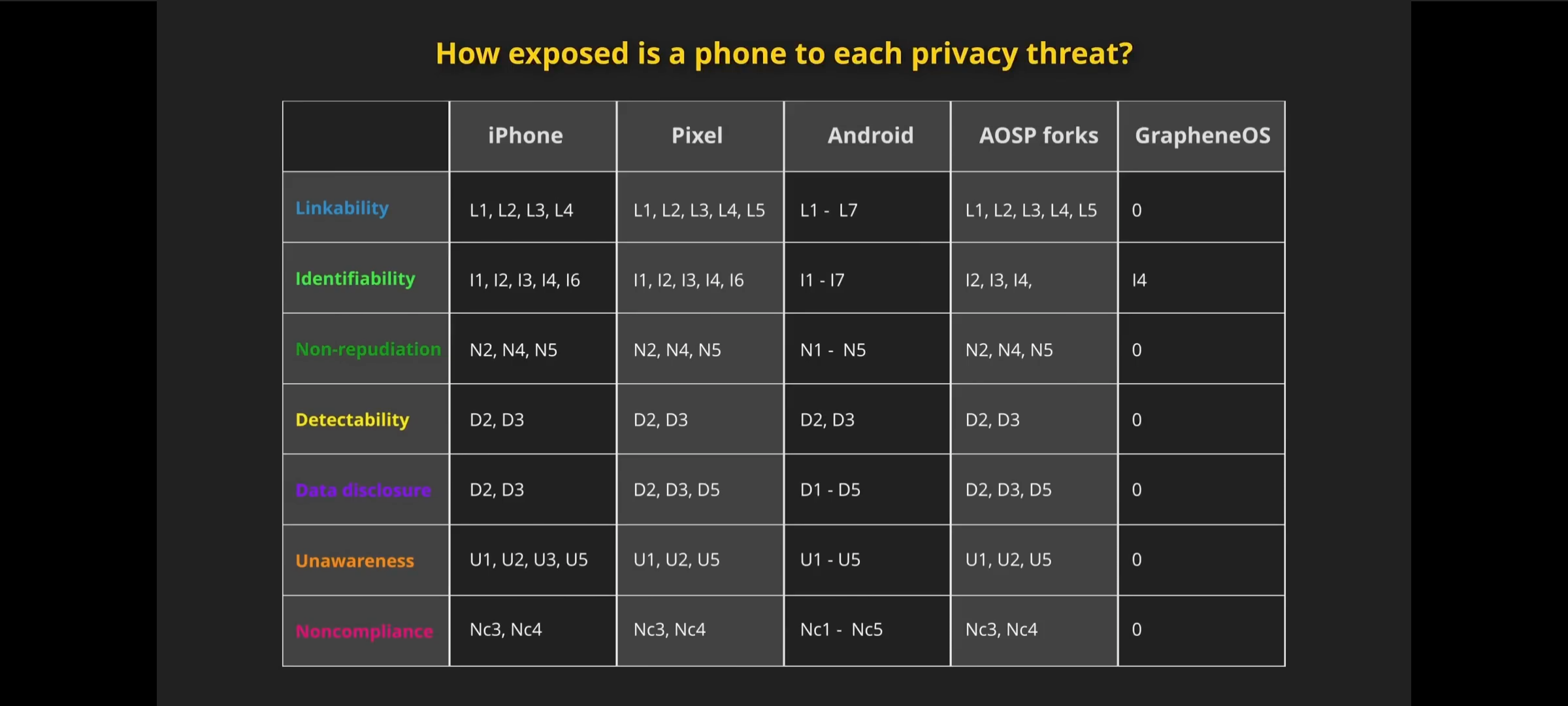
For example, the Pixel, AOSP and Android are given several undeserved points due to lack of proper information or understanding of how certain features work. I imagine this is the case too for the iPhone; if a bit less so.
The review apparently doesn’t deep dive into settings or attempt to maximize privacy by turning off unwanted ‘features’ when settings switches are available to the user; nor does it assume that you set up accounts in as private of a manner as reasonably possible or toggle off as many default-on consent switches as needed.
While I would support scoring and dinging each case or instance for “Privacy Settings that don’t actually work”…this video really doesn’t do a lot of legwork and leans on the anecdotal evidence of scary news stories too much.
Worse was the fact that the entire video felt like they were shilling for Graphene OS; which is known to have a slightly unfriendly maintainer and community surrounding him to say the least.
No mention of Lineage or other privacy oriented Android ROMs were analyzed. AOSP too, was unfairly lumped in and dinged for specific points of the Default Pixel configuration…and yes there are major differences between AOSP and Pixel Android; even though Google tries to be less in-your-face invasive than the other OEMs. Not enough credit is given for the “On-Device” smart features implemented properly on the Pixels.
Out of personal experience; I’d actually rate a proper Lineage OS install of 4 whole Android versions ago to be more private than stock. Not quite as private as Graphene; but not quite as invasive and much more enforcing of privacy. The debloating provided by a clean AOSP-like ROM, such as Lineage, as opposed to a “Stock Android” configuration from a major OEM is stark.
Most importantly I personally feel that the privacy model chosen for the video is far too thickly detailed for an average person. Most of the privacy concerns listed on each card contained concern points that might only tangentally apply or don’t apply at all to mobile phones. The way that each card was scored and applied felt low effort. None of the points on any of the card(s) were weighted with average users in mind.
I really hope someone goes into a much deeper dive; this video is basically clickbait that parrots the commonly parroted advice in the privacy community; which isn’t even good advice, it’s just ‘One-Size-Fits-All’ style advice which gives the user no room to make necessary ‘Privacy vs Convenience’ tradeoffs that they themselves could have made if they understood proper threat modelling.
I’d actually rate a proper Lineage OS install of 4 whole Android versions ago to be more private than stock.
Its always the lineageos stans that can’t take the truth.
Would a research paper change your mind?
https://infosec.exchange/@rene_mobile/113431029855652363
According to this table, Google Pixels beat other devices listed there by far. Even Samsung S-series doesn’t look good
What about a security expert?
Overall, LineageOS does not leave a privacy-friendly or truly secure impression
TL;DR: I think this video oversimplifies the analysis according to the cards and gives Graphene OS undue weight without going into sufficient detail as to why each scored under each category.
i use a customization-oriented aosp custom rom (vanilla version, no google). It is already very private but there is more private than this, but that seriously restricts usability and visual appeal
if you have a xiaomi phone with GrapheneOS, NEVER, REALLY, NEVER!! relock the bootloader
That’s the case with most non-Google phones
How did you install Graphene in the first place?
i didn’t, but it is possible, altrough, not straightforward and requires some knowledge. I have an aosp-based custom rom, vanilla InfinityXOS (previously Superior-Extended). I have Poco X3 Pro btw. And because of how bootloader unlocking works, it is not a two-way process on xiaomi devices. Once you unlock it, there is no going back. If you try, it will hard brick and you can get a JTAG or something to reprogram the soc capacitors (doesn’t worth trying, there isn’t any single known xiaomi phone that didn’t brick upon an attempt to relock the bootloader)
That’s really cool! And yeah the bootloader locking checks out with into from other guides.
That unbricking talk flies over my head on the other hand, it sounds like one of those fake tech speaks to my uncultured self lol
I agree with this. However the very latest Pixels (with the stock ROM) might be a bit more invasive than the phones by an OEM like Motorola or Nokia.
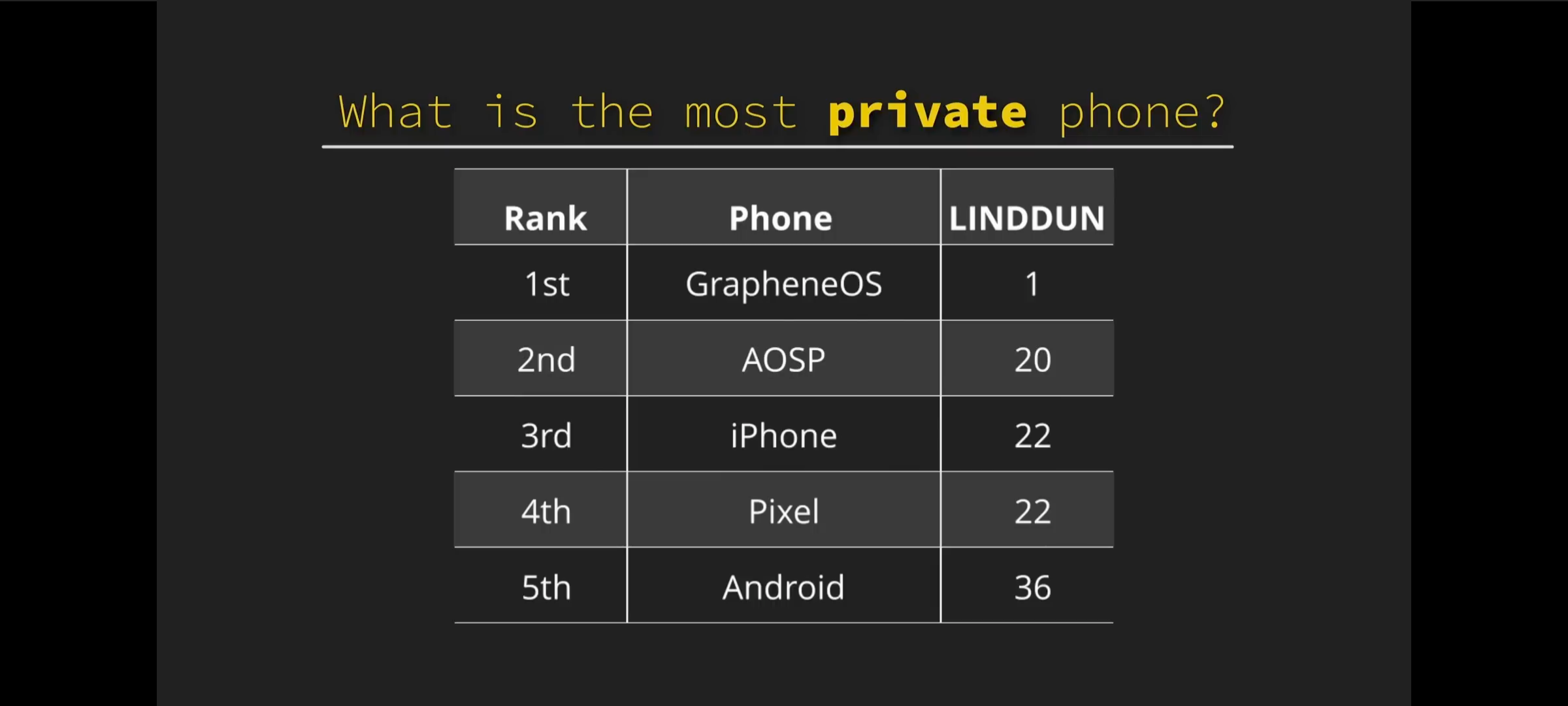
TL;DR: Out of iPhone, Pixel, Android, AOSP forks, and GrapheneOS, the answer is GrapheneOS by a country mile.
Actually good point, added a TLDW screenshot of the summary
Four seconds of reading Vs a 16 minute video
If you want to hear the “why” part, that’s the 16m
GrapheneOS sometimes sacrifices privacy for security.
I had way more privacy related features and controls on a rooted LineageOS phone (which was obviously much less secure)
Please elaborate and/or [Citation needed].
Such as? Been thinking of flashing GrapheneOS since I got a Pixel on the way.
This is incorrect. It strengthens both privacy and security in a lot of ways for an average user.
share your data with bad actors to prevent bad actors from getting your data
Which of these smart phones lets me have a headphone jack… ’cause that is how I will choose. I can patch software & be wary about how I use the device, but I can’t just add I/O to the hardware. Until the Pixel brings back the jack, it is dead to me.
I got a Nokia XR20 because of this. Also waterproof and rugged. A phone that needs a case to survive the hairless monkeys dropping it is a design failure and completely unacceptable.
Just wish I could use proper software with it.
Rotary.
Not really. A smartphone with a privacy-respecting OS and E2EE communication apps only is more secure. Though you can argue that it’s not really a phone if you don’t use the soter service.
Tin cans and string
The tin can phone inherently provides end-to-end encryption. The acoustic signals, which are essentially longitudinal mechanical vibrations, travel directly through a taut string or wire. This physical medium ensures that the sound waves are converted into mechanical vibrations at the transmitting end and reconverted into sound at the receiving end, effectively eliminating any possibility of electronic eavesdropping or interception.
One of the most significant advantages of the tin can phone is its complete absence of a digital footprint. Unlike modern telecommunication devices that rely on electronic signals and data packets, tin can phone operates purely on mechanical principles. This means there are no digital records, metadata, or logs that can be hacked, traced, or subpoenaed.
The simplicity of the tin can phone renders it immune to a wide array of cyber threats. There are no software vulnerabilities, no firmware to update, and no risk of malware or ransomware attacks. The device’s operation is entirely analog, relying on the physical properties of sound waves and mechanical vibrations, making it impervious to digital exploits.
The physical nature of the tin can phone also contributes to its security. The string must be kept taut for effective communication, and any attempt to tap into the line would be immediately noticeable due to the loss of tension and degradation of sound quality. This provides a built-in tamper-evident feature, ensuring that any unauthorized access attempts are easily detected. On top of that, if someone attempts a man in the middle attack, you should be able to see it happening during the call and act accordingly before any sensitive data gets exposed.
The operational simplicity of the string and cans phone is another layer of security. With no complex interfaces or user authentication mechanisms, the risk of user error leading to security breaches is virtually nonexistent.
Somehow that posted as an entirely empty comment… Here’s what was supposed to be in it:

Your first comment was right: no phone
Spoiler: It’s a banana phone.
What is the most private phone? Take a visit to a Google property and curb stomp your privacy to find out!
I didn’t watch the video but I don’t think there is any phone that lets you avoid having your location tracked. If there is wifi near where you want to use the phone, you could run a voip client on on a wifi-only tablet, perhaps.
I’ve been wondering whether satellite communications gizmos with no GPS allow any type of precise location tracking from the satellite. I’ve been interested in this, which lets you exchange text messages at fairly low cost (about 2 cents per 50 byte unit). Besides possible privacy advantages, it also lets you communicate where there is cell coverage:
Added a TLDW summary to the post if you want to take a peek
Ok but wifi only isn’t really a phone?
Can you call on wifi? Yes (voip numbers like you said). I think that’s a phone.
Obviously you need to be connected
Then my laptop is a phone? It’s sort of a phone but it doesn’t connect to the phone network, so only sort of. Since it needs a wifi signal it’s not so mobile either.
Well technically there is: pixel + graphene os + airplane mode with wifi only, from the video
Usually I tend to avoid sarcastic responses, but since no one mentioned it, how about the game of Telephone?
A flame of xylophone?









